AUTOMATION

June 30
Easy Integration with scripts. .
> Input and output redirection
> Tasks automation
> Batch mode
> Interactive mode
> Import/export of X.509 certificates
> Supports OpenPGP & x.509 certificates
> Conversion between PGP keys and X.509 certificates
> FIPS compliant
> Generation of PKCS #10 Certification Requests
> Password requests automation
View Complete Archive
PlatFORMS
Supported Operating SystemsFreeBSD
Linux on Intel (Redhat/SUSE)
Red Hat Enterprise Linux 5.4 (x86 and x86_64)
Red Hat Enterprise Linux 5.5 (x86 and x86_64)
Red Hat Enterprise Linux 6.0 (x86 and x86_64)
SLES (SUSE Linux Enterprise Server) 10 SP2 (x86)
Solaris 6 SPARC
Solaris 8 SPARC
Solaris 9 (SPARC, 32-bit),
Solaris 10 (SPARC, 32-bit),
Solaris 10 (x86), Solaris 10 (x86_64)
Solaris Intel
Apple Mac OS X
Windows Server 2003 (32-bit and 64-bit)
Windows Server 2008 32-bit
Windows Server 2008 R2 64-bit
Windows 10 (32-bit and 64-bit) Windows XP Professional (32-bit and 64-bit)
Windows Vista (32-bit and 64-bit)
Windows 7 (32-bit and 64-bit)
HP-UX
IBM AIX
IBM z/OS
See the Video

Authora EDGE
Authora's Encrypted Data Gateway Engine, aka "The EDGE" Open PGP Command Line empowers you to elegantly integrate and automate cryptography in your business processes
EDGE Command Line is a scripting and shell-based encryption application that integrates quickly with both off-the-shelf applications and custom scripts and provides advanced key management options that enterprises require for critical automated business process applications, such as securing multisite FTP transfers and encrypting backup tapes for
offsite storage.
Edge helps customers meet encryption requirements with multiple commands for transfer, storage, and backup of sensitive data.
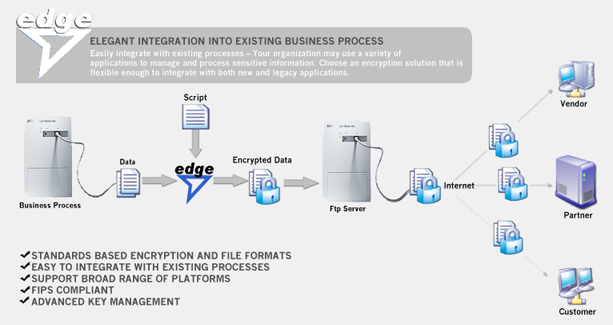 This example shows an implementation of EDGE Command Line by real-life Edge users.
This example shows an implementation of EDGE Command Line by real-life Edge users.
Authora Encrypted Data Gateway Engine (EDGE):
Developed for businesses requiring a way to exchange secure data with branch offices, vendors, and business partners. Exchange electronic data securely and automate protection within applications, file transfers, transaction processes, and email using the strength of Open PGP encryption, (also works with X.509 Certs).
On This Page:
Command Line Customizing
Public-Key Encryption Smart Card
Digital Signatures Trust Zones
FIPS Level 4 Key Management
Open PGP Session Keys
X.509 Platforms
Automating
Maintenance Plans
COMMAND LINE
EDGE is a command-line application that runs on Windows and on a variety of UNIX systems. Every command can be automated and integrated with existing process. EDGE can work on foreground and on background (UNIX background process).
PUBLIC-KEY ENCRYPTION FOR CONFIDENTIALITY
EDGE allows you to send encrypted data using the recipients’ public key for encrypting data. The encrypted data can only be decrypted by the owner of the private key related to the public key used to encrypt the data. By using public-key encryption you eliminate the transfer of the secret password to the recipients and all password management when sending the same message for more than one recipient. Whomever the sender is, the recipient always decrypts the message with the same secret key.
DIGITAL SIGNATURES FOR AUTHENTICATION AND NON-REPUDIATION
EDGE uses public-key cryptography to generate digitally signed data. By using a digitally signed message, the receiver of the message can be sure that the data has not been altered during its transfer. Moreover, the receiver can also be sure who the sender of the message is (proof of identity) by validating the signer’s public key. A digital signature contains a timestamp, informing the receiver when the signature was created.
FIPS LEVEL 4
EDGE follows recommendations published in FIPS 140-2 from NIST (security level 4) in order to accurate the security of the system. For example, power-up tests can be activated to check the integrity of the cryptographic engine. Automatic tests on random numbers cannot be deactivated and work all the time as a red-alert system. If a test fails, EDGE automatically stops with an error.
COMPATIBLE - OPEN PGP STANDARD
EDGE is compliant with the OpenPGP standard, OpenPGP is the most widely used standard for securing emails and secure file transfer. EDGE follows IETF RFC 1991 and IETF RFC 2440. In addition, EDGE uses the same syntax as other OpenPGP command-line product for an easy integration or replacement to an existing solution. A message encrypted with another OpenPGP client can be handled by EDGE. It is also possible to generate encrypted/signed message for older Open PGP clients like PGP 2.6.x or ViaCrypt PGP. For more info see EDGE compatability matrix...>
LEVERAGES X.509 cERTIFICATES
EDGE can use X.509 certificates to encrypt or verify signatures and X.509 secret keys to decrypt and sign messages. It can convert an X.509 certificate to an OpenPGP key to be freely distributed to other OpenPGP users.
On Windows, EDGE can use local X.509 certificates and secret keys to encrypt/decrypt messages.
CONVENTIONAL ENCRYPTION
EDGE allows you to encrypt a message symmetrically using a password.
Even if the recipient has no secret key, you can send your message securely.
CUSTOMIZABLE
EDGE provides options to let you configure the way you want to encrypt/decrypt messages. Everything from the way to get a passphrase to the compression level can be configured. One application matching your way to handle e-business processes.
SMARTCARD SUPPORT
On Windows, EDGE can use Smartcards to sign or to decrypt a message. The secret key stays on a secure support and is accessed only using the software provided by the manufacturer of the Smartcard. Once the Smartcard is removed, there is no way to sign or decrypt messages with that secret key.
TRUST ZONE SUPPORT
EDGE can access multiple Sovereign Trusted Zones for enrollment, elegant public and/or secret key exchange, or to verify keys. Simply specify a Trusted Zone and add trust management to your e-business process.
ELEGANT KEY MANAGEMENT
EDGE provides a set of commands to manage your public and secret keys. You can generate new key pairs, add users, revoke keys and certify other keys, enabling/disabling keys and many other functions.
SESSION KEY SUPPORT
Never compromise your secret key. EDGE allows you to extract the session key from an encrypted file. This session key can be used to decrypt that file only. This option allows you to give access (to decrypt) only the message you choose without compromising your secret key and all other messages already encrypted with your secret key.
PLATFORM INDEPENDENT
o FreeBSD
o Linux on Intel (RedHat/SuSE)
o HP Tru64 UNIX
o HP-UX UNIX
o Solaris Sparc 6, 8 & 9 (both 32 and 64 bits)
o Solaris Intel
o IBM AIX
o MacOS X
o Windows 98, 2000, ME, NT, XP
o For other platforms, please contact us
AUTOMATED
Authora Encrypted Data Gateway Engine automates all operations from compressing, encrypting, and signing of files. On the recipient side, a reverse process can automatically verify the signature, decrypts and decompresses the files.
MAINTENANCE PLANS/ SUPPORT
Maintenance plans (Level 1/Bronze, Level 2/Gold and level 3/Platinum) include support, updates, and upgrades and are available either through a yearly maintenance fee based on purchased license(s) or can also be on a per incident fee.
**maintenance details located here
Integrate Edge into you exisiting business processes and automate Encryption, decryption, digital signing, and verification..





